Its Right There
Write up for Android reverse engineering challenge - part of Square CTF 2022
Description
In this challenge an apk file was provided which had one screen showing the flag zoomed in in such a way that it overflowed into the part of the screen where it was no longer visible.
https://squarectf.com/2022/itsrightthere.html

Therefore you can use a tool called apktool to decompile the apk file using the command
apktool d freeflag.apk
Next to decompile any java files, you can do the following:
dex2jar freeflag/classes.dex
Now use the JD (Java Decompiler) to inspect the source
jd-gui classes-dex2jar.jar
As seen in the decomplied picture we need to remove the highlighted line in order to make the flag visible.
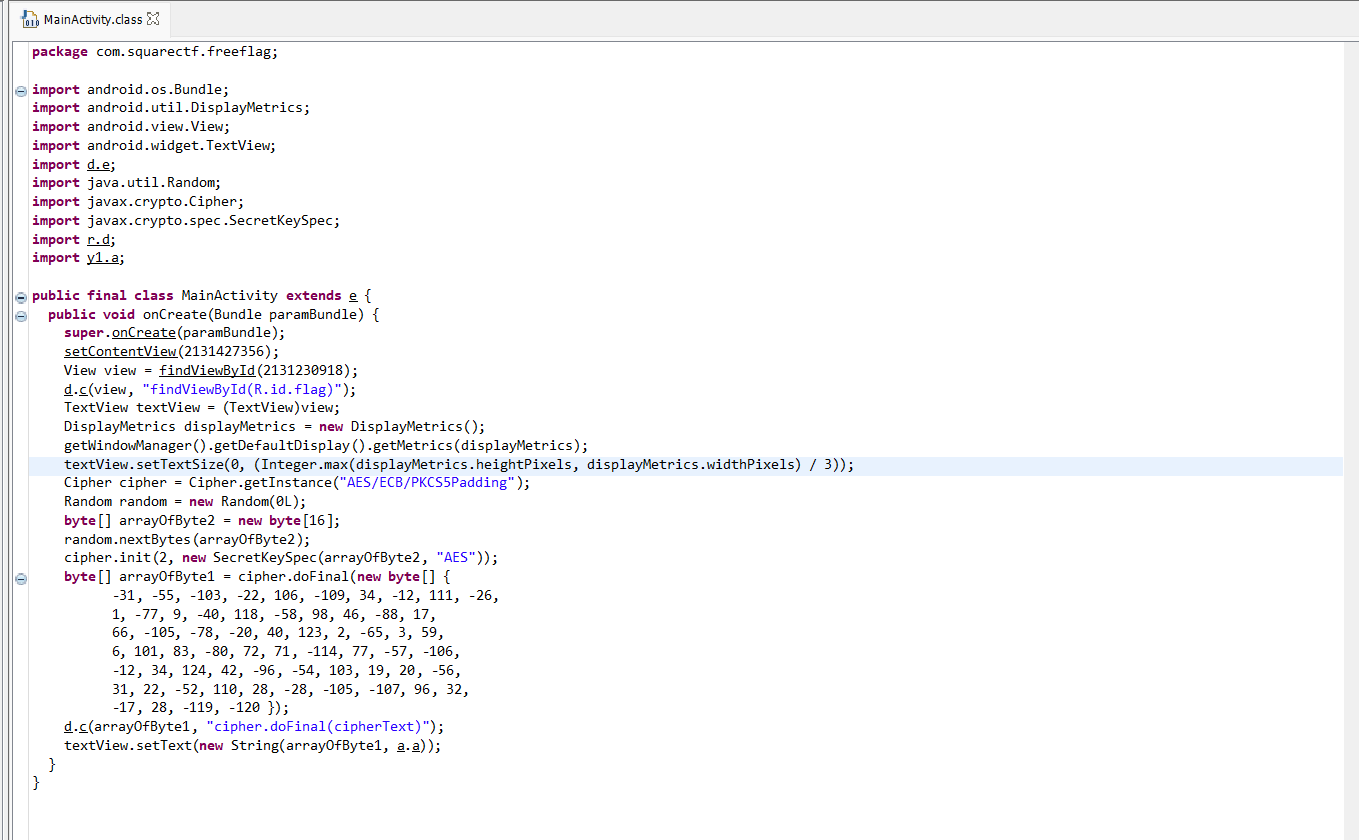
Open the decompiled project in Android studio, here the java files are present as smali where we can see the following highlighted line(see screenshot below) corresponds to the one shown above therefore we need to remove this line.

Once you have made your changes, you need to repack the apk with command
apktool b -f -d freeflag
After recompiling the apk the new apk will be generated in Dist folder.
freeflag — Dist- freeflag.apk
The apk must be signed before you run on your device. Before signing an apk, create a key if you don’t have an existing one using keytool or use the android debug key. If prompted for a password, create your own password.
Now sign the apk with the key:
jarsigner -verbose -keystore androiddebugkey
Finally install the repacked signed apk and launch it for the flag.

Last updated